Authors: Nagalakshmi & Dr.Mohammed Ali Hussain
ABSTRACT:
Finding of a capable means for sharing of partial data within cloud storage is not a slight issue. Cryptographic methods of key assignment minimize expenditure in storage and management of secret keys for common cryptographic use. Cryptographic methods have become flexible and involve numerous keys meant for a single application. We make a study on novel public-key cryptosystems that construct constant cipher-texts such that resourceful delegations of decryption rights for cipher-texts are promising. We initiate an exceptional type of public-key encryption known as key-aggregate cryptosystem in which users encrypts a message in a public-key. Our method is flexible than hierarchical key task that save spaces when the key-holders share a related set of privileges.
Keywords: Key-aggregate cryptosystem, Cryptographic methods, Public-key encryption, Cipher-texts, Cloud storage.
- INTRODUCTION:
Data sharing is important in cloud storage as cloud users will not hold strong conviction that server is carrying out a good job regarding the issue of confidentiality. During consideration of traditional means for ensuring is depending on server to implement access control subsequent to authentication which denotes that any unexpected privilege intensification will expose the entire data [1]. Concerning ease of use of files, there is sequence of cryptographic methods that allows a third-party auditor to make sure accessibility of files in support of data owner devoid of leaking anything about the data. In the techniques of modern cryptography, a basic trouble we come across is with reference to leveraging confidentiality of knowledge to carry out cryptographic functions numerous times. Cryptographic methods are becoming versatile and involve numerous keys meant for a single application. In our work we make a study on making of decryption key more commanding by means of allowing decryption of numerous cipher-texts, devoid of intensifying its size. We study novel public-key cryptosystems that construct constant cipher-texts such that resourceful delegations of decryption rights for cipher-texts are promising. The uniqueness is that one can combine secret keys and put them as single key, however including power of all keys being combined.
- METHODOLOGY:
For designing of an efficient public-key encryption format that manages flexible delegation so that any subset of cipher-texts is decryptable by means of a constant-size decryption key. We build a solution to this problem by introducing a public-key encryption identified as key-aggregate cryptosystem where users encrypt a message in a public-key, and in an identifier of cipher-text known as class [2][3]. Hence cipher-texts are later considered as various classes. The sizes of cipher-text, master-secret key, as well as aggregate key in our key-aggregate cryptosystem schemes are of stable size. The parameter of public system have size linear in number of cipher-text classes, however only some of it is essential each time and it is fetched on demand from huge cloud storage. In our work we recommend several concrete key-aggregate cryptosystem schemes by various levels of security. In our work we study novel public-key cryptosystems that construct constant cipher-texts such that resourceful delegations of decryption rights for cipher-texts are capable. The secret key holder release a continuous size aggregate key for flexible cipher-text set within cloud storage, however other encrypted files outer to the set stay on private and this compact aggregate key is suitably sent to others by extremely restricted secure storage. Methods of cryptographic key assignment minimize expenditure in storage and management of secret keys for common cryptographic use. Utilization of a tree structure, a key for a specified branch is used for deriving of keys of its descendant nodes. For the most of advanced cryptographic key assignment methods maintain access policy that is modelled by means of acyclic graph or else a cyclic graph. The majority of these methods generate keys for symmetric-key cryptosystems, although key derivations might necessitate modular arithmetic as employed in public-key cryptosystems that are more costly than symmetric-key operations. We study on making of decryption key more commanding by means of allowing decryption of numerous cipher-texts, devoid of increasing its size. Generally methods of hierarchical solve problem to some extent when one intends to distribute the entire files in a certain branch in hierarchy. Number of keys enhance with number of branches and is improbable to occur with a hierarchy that set aside number of entire keys to be approved for the entire individuals. Identity-Based Encryption is public-key encryption where public-key of a user is set as a user identity string. There is a trustworthy party known as private key generator in Identity-Based Encryption who holds a master-secret key as well as issue a secret key towards each user regarding user identity. The encryptor takes public parameter as well as user identity to encrypt a message.
- AN OVERVIEW OF PROPOSED SYSTEM:
By mathematical tools, cryptographic methods are becoming versatile and involve numerous keys meant for a single application. We make a learning of novel public-key cryptosystems that construct constant cipher-texts such that resourceful delegations of decryption rights for cipher-texts are promising [4]. The distinctiveness is that one can combine secret keys and build them as compact as single key, however including power of all keys being combined. We introduce a special type of public-key encryption known as key-aggregate cryptosystem in which users encrypts a message in a public-key. Our approach is flexible than hierarchical key task that save spaces when the key-holders share a related set of privileges.
In techniques of recent cryptography, a basic trouble we come across is with reference to leveraging confidentiality of knowledge to carry out cryptographic functions numerous times. Designing of our basic proposal is motivated from collusion-resistant broadcast encryption system that is projected by Boneh et al. While their system supports stable size secret keys that contain power for decryption of cipher-texts that are connected to a particular index. In the proposed approach secret key holder release a continuous size aggregate key for flexible cipher-text set within cloud storage, however other encrypted files outer to the set stay on private and this compact aggregate key is suitably sent to others by extremely restricted secure storage. A key-aggregate encryption system consists of algorithms such as: data owner starting public system parameter by means of Setup and produces a master-secret key pair by the use of KeyGen. Messages are encrypted by the use of Encrypt.
The data owner can make use of master-secret to make an aggregate decryption key meant for a set of cipher-text classes by the use of Extract. The generated keys are passed to delegates securely. Any user by means of an aggregate key decrypts any cipher-text that is provided that cipher-text class is controlled in aggregate key by means of Decrypt. Getting of consistent size aggregate key as well as stable size cipher-text at the same time comes from linear-size system parameter that is generated by a trustworthy party, shared among the entire users and still hard-coded to user program. While the users require trusting parameter-generator for strongly erasing used ephemeral values, access control is still guaranteed by means of a cryptographic mean rather than relying on various servers to confine accesses frankly [5][6]. While novel public-key is basically treated as a novel user, one might have concern that aggregation of key all across two self-determining users is not promising. Local aggregation indicating the secret keys in same branch can constantly be aggregated can be achieved.
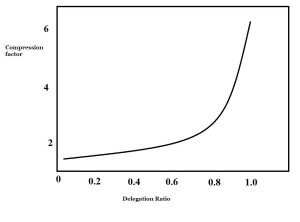
Fig1: An overview of relationship among compression factor as well as delegation ratio.
- CONCLUSION:
We initiate a unique type of public-key encryption identified as key-aggregate cryptosystem in which users encrypts a message in a public-key. Our technique is efficient than hierarchical key task that save spaces when the key-holders share a related set of privileges. The most of higher cryptographic key assignment methods preserve access policy that is modelled by means of acyclic graph or else a cyclic graph. The mainstream of these methods produce keys for symmetric-key cryptosystems, although key derivations might necessitate modular arithmetic as employed in public-key cryptosystems that are more costly than symmetric-key operations. In the procedures of current cryptography, a basic trouble we come across is with reference to leveraging confidentiality of knowledge to carry out cryptographic functions numerous times. In our work we make a study of decryption key more commanding by means of allowing decryption of numerous cipher-texts, devoid of intensifying its size. We learn public-key cryptosystems that construct constant cipher-texts such that resourceful delegations of decryption rights for cipher-texts are promising. The distinctiveness is that one can combine secret keys and build them as compact as single key, however including power of all keys being combined.
REFERENCES
[1] D. Boneh and M.K. Franklin, “Identity-Based Encryption from the Weil Pairing,” Proc. Advances in Cryptology (CRYPTO ’01), vol. 2139, pp. 213-229, 2001.
[2] A. Sahai and B. Waters, “Fuzzy Identity-Based Encryption,” Proc. 22nd Int’l Conf. Theory and Applications of Cryptographic Techniques (EUROCRYPT ’05), vol. 3494, pp. 457-473, 2005.
[3] S.S.M. Chow, Y. Dodis, Y. Rouselakis, and B. Waters, “Practical Leakage-Resilient Identity-Based Encryption from Simple Assumptions,” Proc. ACM Conf. Computer and Comm. Security, pp. 152-161, 2010.
[4] C.-K. Chu, J. Weng, S.S.M. Chow, J. Zhou, and R.H. Deng, “Conditional Proxy Broadcast Re-Encryption,” Proc. 14th Australasian Conf. Information Security and Privacy (ACISP ’09), vol. 5594, pp. 327-342, 2009.
[5] S.S.M. Chow, J. Weng, Y. Yang, and R.H. Deng, “Efficient Unidirectional Proxy Re-Encryption,” Proc. Progress in Cryptology (AFRICACRYPT ’10), vol. 6055, pp. 316-332, 2010.
[6] G. Ateniese, K. Fu, M. Green, and S. Hohenberger, “Improved Proxy Re-Encryption Schemes with Applications to Secure Distributed Storage,” ACM Trans. Information and System Security, vol. 9, no. 1, pp. 1-30, 2006.