Authors: Nagalakshmi & Dr.Mohammed Ali Hussain
ABSTRACT:
Various alternative solutions occur for storage services, whereas data solutions of confidentiality for database as a service concept are still immature. We recommend a new structure that integrates services of cloud database with data privacy as well as option of executing simultaneous operations on encrypted information. We learn secure database as a service as efficient solution to permit cloud tenants which support geographically distributed clients to join directly to encrypted cloud database, carry out autonomous operations. It provides advantage of database as service merits, for instance flexibility and scalability, devoid of revealing unencrypted data towards cloud provider. The proposed system has advantage of elimination of intermediate proxies that limit flexibility, accessibility, and scalability features that are inherent in cloud based solutions. Secure database as a service construct conventional cryptographic schemes, isolation methods, for managing of encrypted metadata on cloud database.
Keywords: Secure database as a service, Cloud database, Metadata, Cryptographic schemes, Cloud provider, Data privacy.
- INTRODUCTION:
There are a number of works that ensure confidentiality for storage as a service concept. However assuring of privacy in database as a service is still a challenge in research works. Hence we make an effort to study secure database as a service as the efficient solution to permit cloud tenants to get advantage of database as a service merits, for example flexibility and scalability, devoid of revealing unencrypted data towards cloud provider. In our work we propose a new structure that integrates services of cloud database with data privacy as well as option of executing simultaneous operations on encrypted information. This solution support geographically distributed clients to join directly to encrypted cloud database, carry out autonomous operations [1]. Different from the architecture of secure database as a service that depend on trustworthy intermediate proxy do not manage distinctive cloud situation where clients issue data structure alterations to a cloud database. It offers a number of original features that distinguish it from earlier work in field of security for distant database services. The secure database as a service is personalized towards cloud platforms and does not set up any intermediary proxy among client and cloud provider. Elimination of any trustworthy intermediate server permits secure database as a service to attain identical consistency, as well as flexibility levels of cloud database as a service [2][3]. Several experiments made on actual cloud platforms reveal that secure database as a service is instantly appropriate to database as a service since it necessitates no alteration to cloud database services. Various methods assure some privacy by means of distributing data between different providers and by consideration of secret sharing.
- METHODOLOGY:
A cloud situation, in which important information is positioned in infrastructures of untrustworthy third parties, making sure of data privacy is of vital importance. Placing of important data in cloud provider have to assure security as well as availability. The possibility of combining consistency, as well as flexibility of a representative cloud database as a service by data confidentiality is verified all the way through secure database as a service that maintain implementation of independent operations to distant encrypted database from numerous geographically distributed clients. For attaining of these objectives, secure database as a service put together conventional cryptographic schemes, isolation methods, for managing of encrypted metadata on cloud database. We study a structure that integrates services of cloud database with data privacy as well as option of executing simultaneous operations on encrypted information. Hence we attempt to study secure database as a service as the efficient solution to permit cloud tenants to get advantage of database as a service merits, for example flexibility and scalability, devoid of revealing unencrypted data towards cloud provider. The proposed structural design has advantage of elimination of intermediate proxies that limit flexibility, accessibility, and scalability features that are inherent in cloud based solutions. Secure database as a service relates closely encryption for protecting data that is managed by untrustworthy databases. It provides quite a lot of original features that distinguish it from earlier work in field of security for distant database services. It assures data privacy by means of allowing a cloud database server to carry out concurrent SQL operations. Secure database as a service attains identical consistency, as well as flexibility levels of cloud database as a service since it does not necessitate any intermediate server. Several clients, probably geographically distributed, can access separately a cloud database service [4]. It does not necessitate a trusted broker since tenant data as well as metadata stored by cloud database are constantly encrypted. It is well-suited with most accepted relational database servers.
- AN OVERVIEW OF DESIGNING OF PROPOSED SYSTEM:
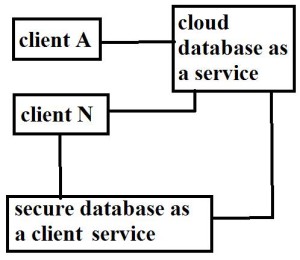
We suggest a new structure that integrates services of cloud database with data privacy as well as option of executing simultaneous operations on encrypted information. It relates closely encryption for protecting data that is managed by untrustworthy databases and support geographically distributed clients to join directly to encrypted cloud database, carry out autonomous operations. Secure database as a service is intended to permit numerous as well as autonomous clients to join directly to untrustworthy cloud database as a service devoid of any intermediate server. In fig1 we assume that a tenant organization obtains cloud database service from an untrustworthy database as a service provider. The tenant subsequently deploys one or additional machines and set up a database as a service client that allows a user to bond to cloud database as a service to manage it, to read as well as write data, and even to make and adjust database tables subsequent to creation. The likelihood of combining consistency, as well as flexibility of a representative cloud database as a service by data confidentiality is verified all the way through secure database as a service. We assume similar security representation that is usually adopted by literature where tenant users are trustworthy, and cloud provider is honest-but-curious. Hence tenant data, data structures, as well as metadata have to be encrypted earlier than exiting from client.
The proposed system is personalized towards cloud platforms and does not set up any intermediary proxy among client and cloud provider. The system has benefit of elimination of intermediate proxies that limit flexibility, accessibility, and scalability features that are inherent in cloud based solutions. The information that is supervised by secure database as a service includes encrypted data, plaintext data, encrypted metadata and metadata. The system does not require a trusted broker since tenant data as well as metadata stored by cloud database are constantly encrypted [5]. To prevent an untrustworthy cloud provider from violation of privacy of tenant data stored in plain form, secure database as a service put together conventional cryptographic schemes, isolation methods, for managing of encrypted metadata on cloud database.
The proposed system attains identical consistency, as well as flexibility levels of cloud database as a service since it does not necessitate any intermediate server. Quite a lot of experiments made on actual cloud platforms make known that secure database as a service is instantly appropriate to database as a service since it necessitates no alteration to cloud database services. Clients of proposed system construct a set of metadata that consist of information that is needed to encrypt in addition to decrypting of information as well as other administration information. Proposed system of secure database as a service recommend a different approach where the entire data as well as metadata are stored the cloud database [6].
Fig1: Structure of secure database as a service.
- CONCLUSION:
Here we propose a structure that put together services of cloud database with data privacy as well as option of executing simultaneous operations on encrypted information. We study secured database as a service to authorize cloud tenants to obtain advantage of database as a service merits, for example flexibility and scalability, devoid of revealing unencrypted data towards cloud provider. This solution maintains geographically distributed clients to connect directly to encrypted cloud database, carry out autonomous operations. The design has benefits of elimination of intermediate proxies that limit flexibility, accessibility, and scalability features that are inherent in cloud based solutions. The secure database as a service is personalized towards cloud platforms and does not set up any intermediary proxy among client and cloud provider. Numerous experiments made on real cloud platforms disclose that secure database as a service is instantly appropriate to database as a service since it necessitates no alteration to cloud database services.
REFERENCES
[1] H. Hacigu¨mu¨ s¸, B. Iyer, C. Li, and S. Mehrotra, “Executing SQL over Encrypted Data in the Database-Service-Provider Model,” Proc. ACM SIGMOD Int’l Conf. Management Data, June 2002.
[2] J. Li and E. Omiecinski, “Efficiency and Security Trade-Off in Supporting Range Queries on Encrypted Databases,” Proc. 19th Ann. IFIP WG 11.3 Working Conf. Data and Applications Security, Aug. 2005.
[3] E. Mykletun and G. Tsudik, “Aggregation Queries in the Database-as-a-Service Model,” Proc. 20th Ann. IFIP WG 11.3 Working Conf. Data and Applications Security, July/Aug. 2006.
[4] E. Damiani, S.D.C. Vimercati, S. Jajodia, S. Paraboschi, and P. Samarati, “Balancing Confidentiality and Efficiency in Untrusted Relational Dbmss,” Proc. Tenth ACM Conf. Computer and Comm. Security, Oct. 2003.
[5] L. Ferretti, M. Colajanni, and M. Marchetti, “Supporting Security and Consistency for Cloud Database,” Proc. Fourth Int’l Symp. Cyberspace Safety and Security, Dec. 2012.
[6] “Transaction Processing Performance Council,” TPC-C, http:// www.tpc.org, Apr. 2013.