Title: ON-DEMAND SECURE ROUTING PROTOCOL FOR AUTHENTICATION AND DATA INTEGRITY IN MANET
Authors: K.Nivedha, P.M.Sharmila & V.Shobana, 4th Year, Department of ECE
Guide: Mr.B.Ram Kumar, Assistant Professor
College: Karpagam Institute of Technology, Coimbatore
ABSTRACT – A mobile ad hoc network consists of mobile nodes that communicate in an open wireless medium. Adversaries can launch analysis against the routing information embedded in the routing message and data packets to detect the traffic pattern of the communications; thereby they can obtain the sensitive information of the system, like the identity of a critical node. Privacy-preserving routing is crucial for some ad hoc networks that require stronger privacy protection. A number of schemes have been proposed to protect privacy in ad hoc networks. However, none of these schemes offer complete unlinkability or unobservability property since data packets and control packets are still linkable and distinguishable in these schemes. In this paper, we define stronger privacy requirements regarding privacy-preserving routing in mobile ad hoc networks. Then we propose an unobservable secure routing scheme On-Demand Secure Routing Protocol to offer complete unlinkability and content unobservability for all types of packets. On- Demand secure Routing protocol is efficient as it uses a novel combination of group signature and ID-based encryption for route discovery. Security analysis demonstrates that OSRP can well protect user privacy against both inside and outside attackers. On-Demand Secure Routing Protocol is implemented on ns2, and evaluate its performance by comparing with Ad-hoc On Demand Distance Vector and MASK. The simulation results show that On-Demand Secure Routing Protocol not only has satisfactory performance compared to Ad-hoc On Demand Distance Vector, but also achieves stronger privacy protection than existing schemes like MASK.
KEYWORDS – Privacy-preserving routing, unobservability, ID-based encryption
I. INTRODUCTION
Mobile Ad Hoc Network is a network in which a set of mobile nodes communicate directly with one another without using an Access Point (AP) or any connection to a wired network. The nodes are free to move randomly and organize themselves arbitrarily. Every node communicates via wireless radios that have limited transmission efficiencies. Due to this limitation on transmission, not all nodes are within the transmission range of each other. If a node wants to communicate with another node outside its transmission range, its mandatory that it needs the help of other nodes in building up a multi-hop route. An important challenge in MANET is that communication has to be made possible by changing network topology due to node mobility.
Despite all its advantages, mobile ad hoc network has the potential vulnerability by means of misbehaving nodes. A node can misbehave and fail to establish route or route the data due to its malicious nature to disrupt the network and take control of the system. Misbehaving node deeply impacts a node’s anticipation of other’s behaviour and decisions during interaction.
The contribution of our paper is:
• A thorough analysis of existing anonymous routing schemes and demonstrate their vulnerabilities.
• To analyze the routing protocols based on mobility models.
• To reduce the effect of attackers .
• To develop the authentication based security scheme in the network.
• To compare the performance of routing protocols in terms of the delivery ratio.
SECURITY GOALS OF AD HOC NETWORKS
ANONYMITY
• User anonymity is implemented by group signature which can be verified without disclosing anyone’s identity. Group signature is what is used to establish session keys between neighbouring nodes, so that they can authenticate each other anonymously. And subsequent routing discovery procedure is built above these session keys. Hence OSRP fulfils the anonymity requirement under both passive and active attacks, as far as the group signature is secure.
UNLINKABILITY
• Let’s consider the three types of packets. In these packets, they are identified by pseudonyms which are generated from random nonce along with secret session keys. The nonces and pseudonyms are never reused, they are used only once. Exception of that of the random nonce and the pseudonym, the remaining part of the message, which includes the trapdoor information in the route request, is decrypted and encrypted at each hop. Hence even for global adversaries who can eaves drop every transmission within the network, it is impossible for him to find linkage between messages without knowing any encryption key. He will have no idea about the type of the packet being transmitted in the network, also he cannot relate different packets in terms of packet type.
• The only way to gain information on relationship between Transmissions is that the attacker has access to some encryption keys by compromising one or more valid nodes.
UNOBSERVABILITY
• In OSRP, RREQ, RREP and data packets are indistinguishable from dummy packets to a global outside adversary. Also, the nodes involved in the routing procedure are anonymous to other valid nodes. Consequently, OSRP provides unobservability as defined for ad hoc networks.
• First of all, a global adversary cannot distinguish different packet types, and neither can he distinguish a meaningful cipher text from random noise. Moreover, the nonce is choosen randomly by any node and never reuses it. The nonce is updated each time after it is used, so there is no linkage between the pseudonyms which are calculated from nonces. Only those mobile nodes with a valid session key can recognize valid pseudonyms and decrypt the corresponding cipher texts to obtain meaningful plaintexts from them.
• Secondly, a node and its next-hop node or previous-hop node on route establish a session key anonymously, hence no one will be able to find out the real identities of its next-hop node or previous-hop node. Even the source and the destination node do not know real identities of the intermediate nodes on route.
• Based on the content unobservability provided by OSRP, Traffic padding can be introduced into the network to thwart traffic analysis and provide traffic pattern unobservability.
NODE COMPROMISE
• Node compromise is easy for the Adversary and highly possible in ad hoc networks, hence it is crucial for a privacy-preserving routing protocol to withstand security attacks due to node capture.Suppose a node is compromised by an attacker, his private signing key and ID-based encryption key are disclosed to the attacker. The attacker now is able to establish keys with neighbouring nodes, but only the following information can be obtained by the attacker:
1) The type of a received packet
2) Data or RREP packets sent to or via the compromised node
3) The headers of the packets relayed by the compromised node
4) RREQ packets sent from the compromised
node’s neighbours. The attacker is not able to gain
more beyond this information.
ATTACKS
COLLUSION ATTACKS
• For the intruding outsiders, privacy Information is completely protected with OSRP. As the attacker is unable to distinguish a meaningful packet from a dummy Packet, OSRP can provide complete protection for privacy with an appropriate traffic padding technique. Even if the target node is encompassed by more than one attack node, given the assumption that no node is totally surrounded by compromised nodes, the attacker is unable to perceive anything except some random dummy packets.
• If appropriate dummy traffic is injected into the network, the colluding outsiders cannot gain any privacy information about the network at all. For the colluding insiders, OSRP still offers unobservability as promised. Though information disclosure is unavoidable for colluding insiders, and the adversary knows a few keys, and the information that the colluding insiders can gain is largely restricted by OSRP.
The attackers are able to know:
1) A target node is involved in a route discovery procedure since it is broadcasting a RREQ packet
2) A target node is the previous hop or the next hop on a path. However, the colluding insiders are not able to know identity of the target node or other intermediate nodes on route. According to the design of OSRP, authentication and key establishment is achieved by group signature, which perfectly protects user identity from disclosure. Consequently, unobservability is guaranteed by OSRP under colluding insider attacks according to the definition of unobservability.
SYBIL ATTACKS
• In the Sybil attack, a single node presents multiple fake identities to other nodes in the network. Sybil attacks is subjected to a great threat to decentralized systems like Peer-to-peer networks and geographic routing protocols. In OSRP, the centralized key server generates group signature signing keys and ID-based keys for network nodes.
• Thus, it is impossible for the adversary to obtain other valid identities except the compromised ones. Nevertheless, the anonymity feature of OSRP allows the adversary to launch Sybil attacks which are similar to collusion attacks discussed above. USOR is able to count such attacks effectively.
II. PREVIOUS WORK
Dezun Dong et.al [16] proposed a topological detection on wormholes in wireless ad-hoc and sensor networks. Wormhole attack is the most sensitive and severe attack regarding the security threats in ad hoc and sensor networks. In a wormhole attack, the attackers tunnel the packets between distant locations in the network through an in-band or out-of-band channel. In a wormhole attack there is an illusion between two distant nodes that they are close to each other. The wormhole can attract and bypass a large amount of network traffic, and thus the attacker can collect and manipulate network traffic. Such a position is exploited by the attacker to launch a variety of attacks, such as drooping, or corrupting the relayed packets, that significantly imperils a lot of network protocols including routing, localization etc. In this paper the adversary does not possess any valid network identity.
Karim El Defrawy, and Gene Tsudik [14] proposed an anonymous location-aided routing in suspicious manets Research in various aspects of mobile ad hoc networks (MANET) during the last two decades has been very active, motivated by military, disaster relief, and law enforcement scenarios. Most commonly in mobile ad hoc networking (MANET) scenarios, the communication between various nodes is based on long-lasting public identities. However, in certain hostile and suspicious settings, node identities must not be exposed and node movements must be untraceable. We use the term “hostile” to mean that communication is being monitored by adversarial entities that are not part of the MANET. Instead nodes need to communicate on the basis of their current locations. ALARM uses nodes’ current locations to securely disseminate and construct topology snapshots and forward data.
Y. Zhang, W. Liu, and W. Lou [13] proposed an anonymous communications in mobile ad hoc networks.Based on present technology, it is a challenging task to provide anonymous communications in mobile ad hoc networks. There are several problems that must be addressed properly. Security and performance concerns are the main challenges. Chaum’s Mix method can effectively prevent an adversary’s attempt of tracing packet routes and hide the source and/or destination of packets. However, applying the Mix method in ad hoc networks may cause significant performance degradation due to its non-adaptive Mix routeselection algorithm. The goal of this project is to develop a Mix route algorithm to find topology- dependent Mix routes for anonymous connections. We have named the protocol that will be implemented MixRoute. The protocol is implemented in ns-2.
Stefaan Seys and Bart Preneel [12] proposed an anonymous routing protocol for mobile ad hoc networks. Wireless transmissions are easy to capture remotely and undetected, while the lack of central management and monitoring make network nodes susceptible to active attacks. It is very obvious that providing anonymity in ad hoc networks is important as users may wish to hide the fact that they are accessing some service or communicating with another user. It is assumed that every node in the network has a permanent Identity that is known by the other nodes in the network that wish to communicate with this node. Next, it is assumed that the source S and the targeted destination D share a secret key kSD and a secret pseudonym. This protocol effectively hides routes in the network, both against a passive global adversary and nodes inside the net work. Because of the probabilistic padding and TTL scheme we use, nodes inside the network will not be able to determine whether the node they received a message from is the source of this message or forwarding it. The advantage of the limited flooding we propose is that it provides dummy traffic where it is needed.
Srdjan Capkun et.al [4] proposed a self-organised public-key management for mobile ad hoc network. In this paper a self-organizing public-key management system is proposed that allows the user to create, store, distribute and revoke their public keys without the help of any trusted authority or fixed server . Here no specific mission is assigned to any subset of nodes. The main problem of any public-key based security system is to make each user’s public key available to others in such a way that its authenticity is verifiable. But in mobile ad hoc networks it’s even more difficult due to the absence of centralized services and networks partitions. Here the user’s the user’s public keys are created by the users themselves. Hence same identifier is used for the user and his node. Key authentication is performed via chains of public-key certificates. To correctly perform authentication via certificate chains, a node needs to check that: 1) all the certificates on the chain are valid (i.e. none of them is revoked) and 2) all the certificates on the chain are correct.
III IMPLEMENTATION OF OSRP ALGORITHM
THE SECURE ON DEMAND ROUTING SCHEME
Unobservable routing scheme consist of two phases : Anonymous key establishment as the first phase and the route discovery process as the second phase. In the first phase , each node employs anonymous key establishment to anonymously construct a set of session keys with each of its neighbours. Then under protection of these session keys, the route discovery process can be initiated by the source node to discover a route to the destination node.
ANONYMOUS KEY ESTABLISHMENT
In this phase, every node in the ad hoc network communicates with its direct neighbours within its radio range for anonymous key establishment. Suppose there is a node S with a private signing key gskS and a private ID-based key Ks in the ad hoc network, and it is surrounded by a number of neighbours within its power range, the anonymous key establishment procedure, S does the following:
Step 1: S generates a random number rs Z*q and computes rsP, where P is the generator of G1. It then computes a signature of rsp using its private signing key gskS to obtain SIGgskS (rSP). Anyone can verify this signature using the group public key gpk. It broadcast rSP, SIGgskS (rSP) within its neighborhood.
Step 2: A neighbor X of S receives the message from S and verifies the signature in that message. If the verification is successful, X chooses a random number rX Z*q and computes rXP. X also computes a signature SIGgskX (rSP|rXP) using its own signing key gskX. X computes the session key kSX = H2(rSrXP), and replies to S with message rXP, SIGgskX (rSP|rXP),EkSX (¯kX*|rSP|rXP), Where kX* is X’s local broadcast key.
Step 3: Upon receiving the reply from X, S verifies the signature inside the message. If the signature is valid, S proceeds to compute the session key between X and itself as kSX = H2(rSrXP). S also generates a local broadcast key kS*, and sends EkSX (kS*|kX*|rSP|rXP) to its neighbor X to inform X about the established local broadcast key.
Step 4: X receives the message from S and computes the same session key as kSX = H2(rS rXP). It then decrypts the message to get the local broadcast key kS*.
PRIVACY-PRESERVING ROUTE DISCOVERY
This phase is a privacy-preserving route discovery process based on the keys established in previous phase. Similar to normal route discovery process, our discovery process also comprises of route request and route reply. The route request messages flood throughout the whole network, while the route reply messages are sent backward to the source node only. If there is a node S (source) intending to find a route to a node D (destination), and S knows the identity of the destination node D. The route discovery process executes as follows:
ROUTE REQUEST (RREQ)
S chooses a random number rS, and uses the identity of node D to encrypt a trapdoor information that only can be opened with D’s private ID based key, which yields ED(S,D, rSP). S then selects a sequence number seqno for this route request, and another random number NS as the route pseudonym, which is used as the index to a specific route entry. To achieve unobservability, S chooses a nonce NonceS and calculates a pseudonym as NymS = H3(kS*|NonceS).
ROUTE REPLY (RREP)
After node D finds out he is the destination node, he starts to prepare a reply message to the source node. For route reply messages, unicast instead of broadcast is used to save communication cost. D chooses a random number rD and computes a cipher text ES(D, S, rSP, rDP) showing that he is the valid destination capable of opening the trapdoor information. A session key kSD = H2 (rSrDP|S|D) is computed for data protection. Then he generates a new pair wise pseudonym NymCD = H3(kCD|NonceD) between C and him. At the end, using the pair wise session key kCD, he computes and sends the following message to C:
NonceD, NymCD , EkCD(RREP,NC,ES(D, S, rSP, rDP), seqno).
MODULE OF PROPOSED SYSTEM
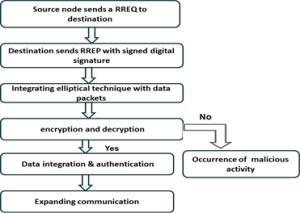
The complete systematic process of the unobservable routing is shown below as a flowchart.
Figure 3.1 Module of proposed system
IV. PERFORMANCE ANALYSIS
We use Network Simulator (NS 2.34) to simulate our proposed on-demand routing technique algorithm. Network Simulator-2(NS2.34) is used in this work for simulation.NS2 is one of the best simulation tools available for Wireless sensor Networks. We can easily implement the designed protocols either by using the oTCL (Tool command Language) coding or by writing the C++ Program. In either way, the tool helps to prove our theory analytically.
A. PERFORMANCE METRICS
We evaluate mainly the performance according to the following metrics.
PACKET DELIVERY LATENCY: It is the time it takes for a specific block of data on a data track to rotate around to the read/write.
PACKET DELIVERY RATIO: It is defined as the ratio of packet received with respect to the packet sent.
NORMALIZED CONTROL BYTES: It is the total bytes of routing control packets transmitted by a node normalised by delivered data bytes, averaging over all the nodes.
The simulation results are presented. We compare our proposed algorithm OSRP with existing schemes like ALARM, ARM .
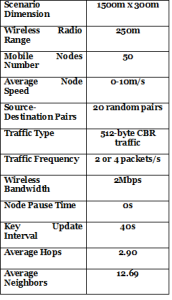
Table1. Simulation settings and parameters of proposed algorithm.
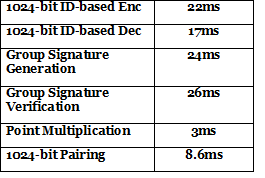
Table2. Parameters on Cryptographic operations
Figure 1. Topology of the proposed scheme
Figure 1 shows that the proposed scheme topology for ensuring the multipath routing. Source node sends the packet to destination node via intermediate nodes. In case if the node failure occurs, the node choose the alternative path to reach correct delivery of packets.
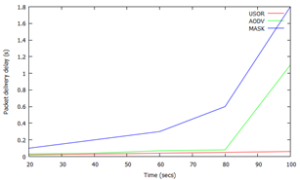
Figure 2. Packet Delivery Delay
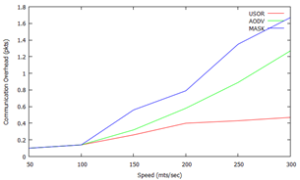
Here speed is taken over a scale of 50 through 300 along the x-axis and plotted against communication overhead over a scale of 0 through 1.8 and the packet delivery delay is compared among the three protocols USOR, AODV, and the MASK. It can be inferred that the packet delivery delay is on a very lower scale compared to MASK and AODV.
In the above graph speed is plotted against the packet delivery delay over a scale of 0 through 1.8. It is compared with the performance of MASK and AODV protocols, which yields a result that USOR has much lower overhead as compared to the other protocols MASK and AODV.
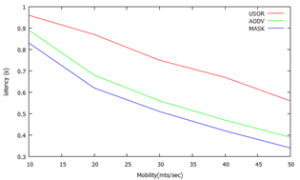
Figure 4. Packet Delivery Latency
Here mobility is plotted in the x-axis against latency along the y-axis from 0.3 through 1 and the packet delivery latency is compared among three protocols USOR,AODV and MASK. It yields a result that USOR has highest packet delivery latency among the three protocols.
V. CONCLUSION
Anonymity is an important part of the overall security architecture for mobile ad hoc networks as it allows users to hide their activities. This enables private communication between users while making it harder for adversaries to focus their attacks. In this paper we first identified a number of problems and strengths in previously proposed solutions. We proposed a solution that provides stronger anonymity properties while also solving some of the efficiency problems. We also provide an analysis of how our protocol achieves its goal.
VI FUTURE WORK
In future, elliptical curve cryptography can be integrated with DSR protocol. Expected outcome can be performed in terms of Packet integrity, Authentication rate, Network connectivity.
REFERENCES
[1] Pfitzmann and M. Hansen(July 2000), “Anonymity, unobservability, and pseudonymity: a consolidate proposal for terminology”.
[2] Y. Zhu, X. Fu, B. Graham, R. Bettati, and W. Zhao(2004),“On flow correlation attacks and countermeasures in mix networks,” in PET04, LNCS3424, pp. 207–225.
[3] D. Chaum(Feb 1981), “Untraceable electronic mail, return addresses, and digital pseudonyms,” Commun. Of the ACM, vol. 4, no. 2.
[4] S. Capkun, L. Buttyan, and J. Hubaux(Jan.-Mar 2003), “Self-organized public-key management for mobile adhoc networks,” IEEE Trans. Mobile Comput.,vol. 2, no.1, pp. 52–64.
[5] J. Kong and X. Hong, “ANODR: aonymous on demand routing with untraceable routes for mobile ad-hoc networks,” in Proc. ACM MOBIHOC’03, pp. 291–302.
[6] B. Zhu, Z. Wan, F. Bao, R. H. Deng, and M. KankanHalli(2004), “Anonymous secure routing in mobile ad-hoc networks,” in IEEE Conference on Local Computer Networks, pp. 102–108.
[7] S. Seys and B. Preneel(2006), “ARM: anonymous routing protocol for mobile ad hoc networks,” in IEEE International Conference on Advanced Information Networking and Applications, pp. 133–137.
[8] L. Song, L. Korba, and G. Yee(2005), “AnonDSR:efficient anonymous dynamic source routing for mobile ad-hoc networks,” in ACM Workshop on Security of Ad-Hoc and Sensor Networks, pp. 33–42
[9] Y. Dong, T. W. Chim, V. O. K. Li, S.-M. Yiu, and C. K.Hui(2009), “ARMR:anonymous routing protocol with multiple routes for communications in mobile ad hoc networks,” Ad Hoc Networks, vol. 7, no. 8, pp. 1536–1550.
[10] A. Boukerche, K. El-Khatib, L. Xu, and L. Korba(2004), “SDAR: a secure distributed anonymous routing protocol for wireless and mobile ad hoc networks,” in IEEE LCN, pp. 618–624.
[11] D. Sy, R. Chen, and L. Bao(2006), “ODAR: on-demand anonymous routing in ad hoc networks,” in IEEE Conference on Mobile Ad-hoc and Sensor Systems.
[12] J. Ren, Y. Li, and T. Li(2009), “Providing source privacy in mobile ad hoc networks,” in IEEE MASS, pp. 332–341.
[13] Y. Zhang, W. Liu, and W. Lou(2005), “Anonymous communications in mobile ad hoc networks,” in IEEE INFOCOM.
[14]K. E. Defrawy and G. Tsudik(2011), “ALARM: anonymous location-aided routing in suspicious MANETs,” IEEE Trans. Mobile Comput., vol. 10, no.. 9, pp. 1345–1358
[15]“Privacy-preserving location-based on-demand routing in MANETs,” IEEE J. Sel. Areas Commun(2011)., vol. 29, no. 10, pp. 1926–1934.
[16] D. Dong, M. Li, Y. Liu, X.-Y. Li, and X. Liao, “Topological detection on wormholes in wireless adhoc and sensor networks,” IEEE/ACM Trans. Netw., vol. 19, no. 6, pp. 1787–1796, Dec. 2011.