Title: OPTICAL WATERMARKING APPROACH FOR PRINTED DOCUMENT AUTHENTIFICATION
Authors: Jadhav Vishwajeet Narayan, ME, Department of Electronics & Telecommunication
Prof.S.D.Mali, Asst.Professor, Department of Electronics & Telecommunication
Prof.S.O.Rajankar, Professor, Department of Electronics & Telecommunication
College: Sinhgad College of Engineering, Ambegaon, Pune
1. ABSTRACT
Forgeries related with official printed documents can easily be performed with the aid of today’s advanced electronic devices such as scanners and computers. The forged documents are usually undetectable by human eyes and it is with this regard that there is an urgent need to find solutions to the threat of counterfeiting of such documents. This article describes a novel visual information concealment approach, referred to as optical watermarking, for the authentication of original printed documents. An optical watermark is a two-dimensional binary image which can be printed on any part of a document and can be of any shape by the superposition of multiple two-dimensional Binary images (referred to as layers) the optical watermark is constructed, with various carrier structural patterns embedding with hidden information. The phase modulation technique is used for embeddeding hidden information into each layer the hidden information becomes visible to the human eyes based on properties of the human visual system and modulation principle only when a right “key” is positioned on top of the optical watermark with the right alignment. The multiple layer structure of the optical watermark makes it extremely robust against reverse engineering attacks. The optical watermark has been applied to various electronic document systems cause its high security and tight links. Online applications are online bill lading, remote sighing and online ticketing. Offline applications are printed high value tickets identification and brand protection.
2. INTRODUCTION
Digital Watermarking is a rapidly developing technology which may be used to provide a certain degree of protection to a digital document from a malicious attack. Digital watermarks provide a means of placing additional information within digital media so that if copies are made, rightful ownership may be determined. Information-hiding techniques have recently become important in a number of application areas. Digital audio, video, and pictures are increasingly furnished with distinguishing but imperceptible marks, which may contain a hidden copyright notice or serial number or even help to prevent unauthorized copying directly. To do so, the techniques used must be robust against the following:
• reverse engineering or cracking of the techniques and methods to obtain all necessary details and to reproduce
the documents or packages in exactly the same way as the authorized parties;
• duplicating the documents or packages without noticeable distortion.
2.1 HIDING INFORMATION
Now a day’s information hiding techniques have attracted a lot of interest, due to offering a certain degree of control by the authorized document producer. Information hiding in printed documents, in principle, is very different from digital watermarking. An article by R. L. van Renesse provides a good review. Here, hidden images (referred to as “latent image”) embedded in a carrier screen image are invisible or illegible to the naked eye but that are visualized or decoded by means of periodic phenomena, such as an absorptive grating, a lenticular screen, or the sampling of a copying system. The term “carrier screen images” is used by many people in this field to imply the fact that the printing of documents is in the form of dot arrays, and that printed images are in the form of halftones. As such, carrier images consist of periodical arrays of screen elements, such as dots and lines, which serve as a carrier on which the encoded information is modulated. In “scramble indicia” by Alasia. Information (text or image) embedded into the carrier image can be verified visually by using a decoder. By modifying dots changing the positions of dot array the information encoded into a carrier image while keeping those changes invisible to naked eyes. Jura’s “Invisible Personal Information (IPI)”, similar to “scramble indicia,” code information by modifying the positions of dots of the carrier image. JURA has now developed “digital” IPI using so-called “Letter- Screen,” by replacing a dots by micro text letters. Assuming that the original carrier image is printed with all dot patterns as letter “0,” and the latent image is coded by changing some “0” into “1” at relevant positions, decoding is achieved simply by computer software by detecting all micro text “1”s. Shimada described a very interesting work for anti-photocopying by using Tri-Branched and Divided Lines. These two line patterns are microstructure lines: Tri-branched line uses three parallel thin lines to replace the original line, while divided lines use many vertical thin short line segments to replace the original line. Because of different optical properties of human eyes and photocopier machines, invisible latent images coded by tri branched and divided lines will become visible as negative images after photocopying. Here, the decoder is the photocopier. Curry further extended the dot pattern to a new rotatable glyph shape for trusted printing applications.
2.2 OPTICAL WATERMARKING
In order to overcome the two main shortcomings of the existing information hiding methods, developed a new information hiding method, referred to as an “optical watermark Normally invisible, a watermark image becomes visible as darker and lighter areas when the paper is held up to the light. Watermarks are still used in quality stationary and have ven been added to currencies of various countries. A watermark is a form, image or text that is impressed onto paper, which provides evidence of its authenticity. Digital watermarking is an extension of this concept in the digital world. In recent years the phenomenal growth of the Internet has highlighted the need for mechanisms to protect ownership of digital media. Exactly identical copies of digital information, be it images, text or audio, can be produced and distributed easily. In such a scenario, who is the artist and who the plagiarist? It’s impossible to tell–or was, until now. Digital watermarking is a technique that provides a solution to the longstanding problems faced with copyrighting digital data. Digital watermarks are pieces of information added to digital data (audio, video, or still images) that can be detected or extracted later to make an assertion about the data. This information can be textual data about the author, its copyright, etc; or it can be an image itself. The digital watermarks remain intact under transmission / transformation, allowing us to protect our ownership rights in digital form. The contributions of work on optical watermarks are as follows.
1) Use of phase-modulation principles to provide the theoretical basis for information hiding in half tone images, with an application to security printing.
2) Provide generalization of the carrier structure from simple dot/line patterns to curves, and further to generic random dot patterns, so as to increase the complexity of carrier patterns, and correspondingly, increase the number of different decoders. This is equivalent to increasing the secret key space.
3) Propose a new concept of a logical carrier image so that the final printed image can be a superposition of multiple logical carrier images (referred to as a watermark layer), each encoded with their own hiding information. The advantage of superposition of multiple watermark layers is that the structure of each carrier image and modulation method is not visible under microscopy and, therefore, it is extremely difficult to reproduce the same.
2.3 APPLICATIONS
The optical watermark technique presented here has been applied to several applications
• Military and intelligence agencies require unobtrusive communications. Even if the content is encrypted, the detection of a signal on a modern battlefield may lead rapidly to an attack on the signaller. For this reason, military communications use techniques such as spread spectrum modulation or meteor scatter transmission to make signals hard for the enemy to detect or jam.
• Criminals also place great value on unobtrusive communications. Their preferred technologies include prepaid mobile phones, mobile phones which have been modified to change their identity frequently, and hacked corporate switchboards through which calls can be rerouted.
• Law enforcement and counter intelligence agencies are interested in understanding these technologies and their weaknesses, so as to detect and trace hidden messages.
• Recent attempts by some governments to limit online free speech and the civilian use of cryptography have spurred people concerned about liberties to develop techniques for anonymous communications on the Internet, including anonymous remailers and Web proxies.
• Marketers use e-mail forgery techniques to send out huge numbers of unsolicited messages while avoiding responses from angry users
3. INFORMATION HIDING BY PHASE MODULATION
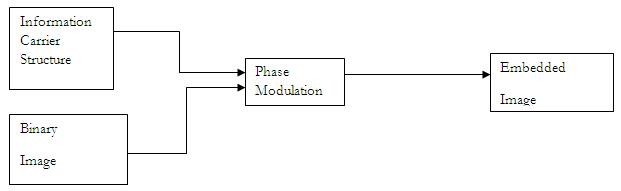
By using phase modulation principle and low pass filter of property of human eyes here we establish a mathematical framework for information hiding. Fig 1 explain the information hiding by phase modulation.
Figure 1: Embedding by Phase Modulation.
3.1 BASIC INFORMATION OF CARRIER STRUCTURE
The basic (or simplest) information carrier structure is chosen to be a dot array, a simple repetitive structure. The dot array can be represented by a reflectance function f0 (x,y) in eqn (1), where Tx and Ty represent the period of the dot array in x and y directions, and Dx and Dy are the width of the dot in two directions .Figure3 shows the Carrier Dot Array Structure implemented by using eqn (1).
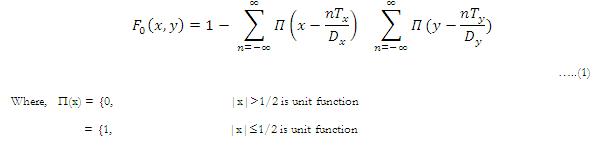
3.2 PHASE MODULATION
For simplicity, we show a latent image embedding by phase modulation along either the x axis or y axis. Figure 3 is an example of such phase modulation. The first latent image, “T,” is modulated in the direction of X axis (as shown in Fig 3), by shifting the “T” image with a half period of dot matrix in the x direction. While the second latent image “T” is modulated in the direction of the Y axis (as shown in Figure 2.
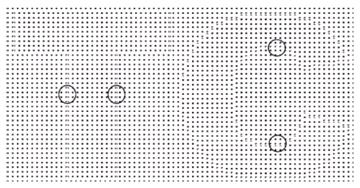
Fig. 2. Modulation of T and C in x axis and y axis, respectively
As shown in the figure, the phase modulation results in visible spatial phase changes on the boundary of the latent images. In order to avoid detection of the modulation at boundaries by the human eye, those denser dots are replaced with specially designed dot patterns, which may use smaller dot sizes or less phase shifts to achieve the similar visual effect as the other no boundary parts. Now let us consider the case that a binary latent image g (x,y) (here, it is the character “T”) to be modulated on one basic information carrier structure in the axis, as shown in Fig. 3. The phase-modulated carrier structure w(x,y) can be written as (2).For the sake of simplicity, we let the phase shift be a half period in (3). It can be easily generalized to the phase shift of any value

3.3. DEMODULATION
Based on the fundamentals of modulation–demodulation, a latent image embedded in an information carrier structure as in (3) can be demodulated when a set of reference line grating with the same frequency is superposed at a right angle. Now showing how demodulation is performed using a set of line gratings. Let us use ( ) to denote the reflectance function of the reference line grating, where θ is the angle between the line rating and y axis and , as shown in Fig. 3.
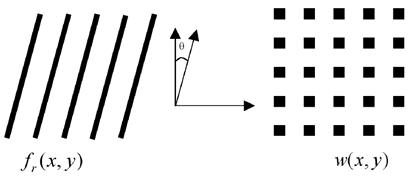
Fig. 3 Reference line grating for demodulation
Where,
Tr and Dr represent the period of the line grating and the width of line, respectively
3.5 MULTIPLE-LAYERED WATERMARK STRUCTURE
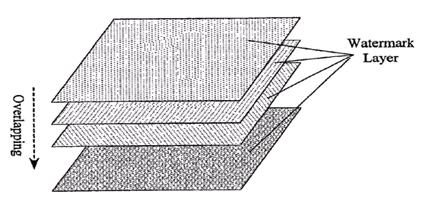
The information hiding method in the previous section is in the context of a “single layer” optical watermark. It is the basic information carrier structure acting as the carrier of the information of latent images. Latent images are phase modulated on the information carrier structure, and cannot be observed by human eyes. Only with the correlative reference line gratings can the embedded latent images be demodulated and become visible to the observer. However, this information hiding method takes advantage of the low-pass filter characteristics of human eyes. In the single-layer case, the “hidden” latent images and embedding methods can still be discovered by investigating the detailed structure of the watermark structure under a microscope.
Figure 4.Super positioned watermark layer
3.6 WATERMARK LAYER
The basic information carrier structure of each watermark layer is a dot array. Let us further incorporate the orientation, and represent a watermark layer as,
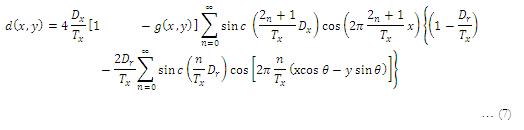
The watermark layer L (fu, fv, Du, Dv, θ, gu, gv) can be considered as a rotated information carrier structure that has frequency fu along u direction and frequency fv along v direction. The size of each dot in the watermark layer is (Du x Dv). There is an angle θ between the Y axis and v direction. This angle is the orientation of the information carrier structure in each watermark layer.
3.7 SUPERPOSITION OF WATERMARK LAYER
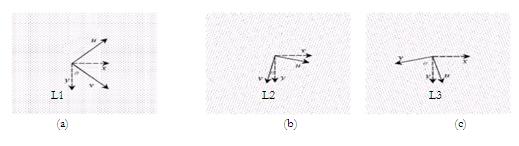
The superposition of multiple watermark layers can be represented as the product of reflectance functions of all watermark layers.

W=L1L2L3
(d)
Figure. 5 Illustration of superposition of multiple watermark layers. (a), (b), and (c) are watermark layers with the same frequency but different orientations. (d) is the superposition of (a), (b), and (c).
Hence, the optical watermark, which is the superposition of N watermark layers, can be represented as,
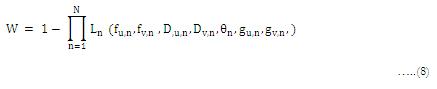
4. CONCLUSION
An optical watermark for printed document authentication is implemented. For optical watermarking the module- Information Hiding by Phase Modulation is implemented .Visual quality of extracted image is tested using demodulation. The superposition of multiple layers effectively protects the optical watermark from reverse engineering individual watermark layers, and significantly enhances the security of the watermark. The work can be extended to improve the quality of extracted watermark.
5. REFERANCES
Hal Berghel, “Watermarking Cyberspace”, Comm. of the ACM, Nov.1997, Vol.40, No.11, pp.19-24.
H. Chabukswar, S. Shefali, “Printed Document Watermarking Using Phase Modulation”, Second International Conference on Emerging Trends in Engineering and Technology, ICETET, 2009.
I. J. Cox and J. P. M. G. Linnartz, “Some General Methods for Tampering with Watermarks”, IEEE Jou.. Selected Areas in Communications, Vol. 16, No. 4, May 1998, pp 587-593.
M.M.Yeung, “Digital Watermarking”, Comm. of the ACM, Jul.1998, Vol.41, No.7, pp.31-33.
S.Bhagya Rekha, T Siva Shankar Reversible Watermarking Method of Digital Images, IJCSET |April 2012.
S.Craver et al., “Can Invisible Watermarks Resolve Rightful Ownership?” IBM Research Report, RC205209, Jul25, 1996.
S. Huang and J.K. Wu, “Optical Watermarking for Printed Document Authentication”, IEEE Trans. on Information Forensics and Security, 2, 2007.