Technical Paper Title: Secure Routing Protocols for Wireless AdHoc Networks
Authors:C.Prasanna lakshmi & K.Yasasvi, 3rd BTech,IT
College: Sri Venkatesa Perumal College of Engineering and Technology
Abstract
A mobile Ad Hoc network (MANET) is a spontaneous network that can be established with no fixed infrastructure. This means that all its nodes behave as routers and take part in its discovery and maintenance of routes to other nodes in the network. Its routing protocol has to be able to cope with the new challenges that a MANET creates such as nodes mobility, security maintenance, quality of service, limited bandwidth and limited power supply. These challenges set new demands in MANER routing protocols.
With the increasing interest in MANETs, there has been a greater focus on the subject of securing such networks. Out of the many discussions and research groups discussing the different security issues in the field of mobile Ad Hoc networks, many papers have been written describing different proposed secure routing protocols that defend against malicious nodes’ attacks that MANET’s face. However, the majority of these MANET secure routing protocols did not provide a complete solution for all the MANET’s attacks and assumed that any node participating in the MANET is not selfish and that it will cooperate to support different network functionalities.
The different existing protocols were surveyed so that to choose one of the secure routing protocols according to its security-effectiveness, study it and analyze its functionality and performance.
Introduction
Wireless Networking
It is an emerging technology that allows users to access information and services electronically, regardless of their geographic position. The use of wireless communication between mobile users has become increasingly popular due to recent advancements in computer and wireless technologies. This has led to lower prices and higher data rates, which are the two main reasons why mobile computing is expected to see increasingly widespread use and applications.
There are two distinct approaches for enabling wireless communications between mobile hosts. The first approach is to use a fixed network infrastructure that provides wireless access points. In this network, a mobile host communicates with the network through an access point within its communication radius. When it goes out of range of one access point, it connects with a new access point within its range and starts communicating through it. An example of this type of network is the cellular network infrastructure. A major problem of this approach is handoff, which tries to handle the situation when a connection should be smoothly handed over from one access point to other without noticeable delay or packet loss.
Fig 1: Infrastructure Network
Another issue is that networks based on a fixed infrastructure are limited to places where there exist such network infrastructures. Figure 1 shows a simple infrastructure network with three nodes.
The second approach is the formation of a wireless Ad Hoc network among users wanting to communicate with each other with no pre-established infrastructure. Laptops and personal digital assistants (PDAs) that communicate directly with each other are examples of nodes in an Ad Hoc network. Nodes in the AdHoc network are often mobile, but can also consist of stationary nodes.
Fig 2: Ad Hoc Network
Each of the nodes has a wireless interface and communicates with others over either radio or infrared channels. Figure 2 shows a simple AdHoc network with three nodes.
Overview of Mobile Ad Hoc Networks:
A mobile Ad Hoc Network (MANET) consists of a set of mobile hosts that carry out basic networking functions like packet forwarding, routing and service discovery without the help of an established infrastructure. Nodes of an Ad Hoc network rely on one another in forwarding a packet to its destination, due to the limited range of each mobile host’s wireless transmissions. An Ad Hoc network uses no centralized administration. This ensures that the network will not cease functioning just because one of the mobile nodes moves out of the range of the others. Nodes should be able to enter and leave the network as they wish. Because of the limited transmitter range of the nodes, multiple hops are generally needed to reach other nodes. Every node in an Ad Hoc network must be willing to forward packets for other nodes. Thus, every node acts both as host and as a router. The topology of Ad Hoc networks varies with time as nodes move, join or leave the network. This topological instability requires a routing protocol to run on each node to create and maintain routes among the nodes.
Mobile Ad Hoc Network Usages
Wireless Ad Hoc networks can be deployed in areas where a wired network infrastructure may be undesirable due to reasons such as cost or convenience. It can be rapidly deployed to support emergency requirements, short-term needs, and coverage in undeveloped areas. So there is a plethora of applications for wireless Ad Hoc networks. As a matter of fact, any day-to-day application such as electronic email and file transfer can be considered to be easily deployable within an Ad Hoc network environment.
Also, we need not emphasize the wide range of military applications possible with Ad Hoc networks. Not to mention, the technology was initially developed keeping in mind the military applications, such as battlefield in an unknown territory where an infrastructure network is almost impossible to have or maintain. In such situations, the Ad Hoc networks having self-organizing capability can be effectively used where other technologies either fail or cannot be deployed effectively. As a result, some well-known Ad Hoc network applications are:
- Collaborative Work: For some business environments, the need for collaborative computing might be more important outside office environments than inside. After all, it is often the case where people do need to have outside meetings to cooperate and exchange information on a given project.
- Crisis-Management Applications These arise for example, as a result of natural disasters where the entire communications infrastructure is in disorder. Restoring communications quickly is essential. By using Ad Hoc networks, a communication channel could be set up in hours instead of days/weeks required for wire-line communications.
- Personal Area Networking and Bluetooth: A personal area Network (PAN) is a short-range, localized network where nodes are usually associated with a given person. These nodes could be attached to someone’s pulse watch, belt, and so on. In these scenarios, mobility is only a major consideration when interaction among several PANs is necessary.
Routing Protocols Overview
Routing in a MANET
Routing in a MANET is fundamentally different from traditional routing found on infrastructure networks. Routing in a MANET depends on many factors including topology, selection of routers, and initiation of request and specific underlying characteristic that could serve as a heuristic in finding the path quickly and efficiently. The low resource availability in these networks demands efficient utilization and hence the motivation for optimal routing in Ad Hoc networks. Also, the highly dynamic nature of these networks imposes severe restrictions on routing protocols specifically designed for them, thus motivating the study of protocols which aim at achieving routing stability.
One of the major challenges in designing a routing protocol for Ad Hoc networks system from the fact that, on one hand, a node needs to know at least the reach ability information to its neighbors for determining a packet route and, on other hand, the network topology can change quite often in an Ad Hoc network. Furthermore, as the number of network nodes can be large, finding route to the destinations also requires large and frequent exchange of routing control information among the nodes. Thus, the amount of update traffic can be quite high, and it is even higher when high mobility nodes are present. High mobility nodes can impact route maintenance overhead of routing protocols in such a way that no bandwidth might remain leftover for the transmission of data packets.
Proactive and Reactive Routing Protocols
Ad Hoc routing protocols can be broadly classified as being Proactive (Table-Driven) or Reactive (On- Demand).
In a Proactive routing protocol, all the routes to each destination are kept in an up-to-date table. Changes in the network topology are continually updated as they occur.
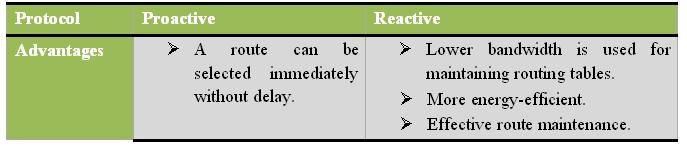
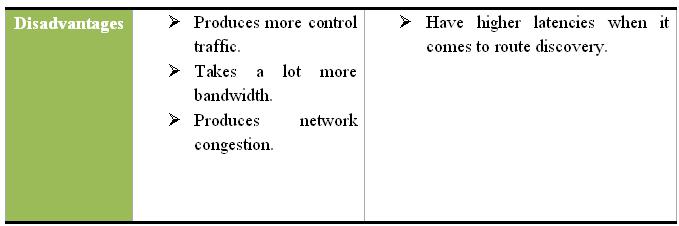
In the Reactive routing protocol, a connection between two nodes is only created when it is asked for by a source. When a route is found, it is kept by a route maintenance procedure until the destination no longer exists or is indeed. The following table 1 presents a comparison between proactive and reactive routing protocols.
Table 1: Proactive Versus Reactive Protocols
Ad Hoc Networks Routing Protocols List
Attacks targeting Routing Protocols
There are basically two types of security threats to a routing protocol, external and internal attackers. An external attacker can be in the form of an adversary who injects erroneous information into the network and cause the routing to stop functioning properly. The internal attacker is a node that has been compromised, which might feed other nodes with incorrect information.
Active and Passive Attacks
Security exposures of Ad Hoc routing protocols are due to two different types of attacks: active and passive attacks. In active attacks, the misbehaving node has to bear some energy costs in order to perform some harmful operation. In passive attacks, it is mainly about lack of cooperation with the purpose of energy saving. Nodes that perform active attacks with the aim of damaging other nodes by causing network outage are considered to be malicious while nodes that perform passive attacks with the aim of saving battery life for their own communications are considered to be selfish.
Malicious and Selfish Nodes in MANETs
Malicious nodes can disrupt the correct functioning of a routing protocol by modifying routing information, by fabricating false routing information and by impersonating other nodes. On the other side, selfish nodes can severely degrade network by simply not participating in the network operation.
In existing Ad Hoc routing protocols, nodes are trusted in that they do not maliciously tamper with the content of protocol messages transferred among nodes. Malicious nodes can easily perpetrate integrity attacks by simply altering protocol fields in order to subvert traffic, deny communication t legitimate nodes (denial of service) and compromise the integrity of routing computations in general. As a result the attacker can cause network traffic to be dropped, redirected to a different destination or to take a longer route to the destination increasing communication delays.
A special case of integrity attacks is spoofing whereby a malicious node impersonates a legitimate node due to the lack of authentication in the current Ad Hoc routing protocols. The main result of spoofing attacks is the misrepresentation of the network topology that possibly causes network loops or partitioning.
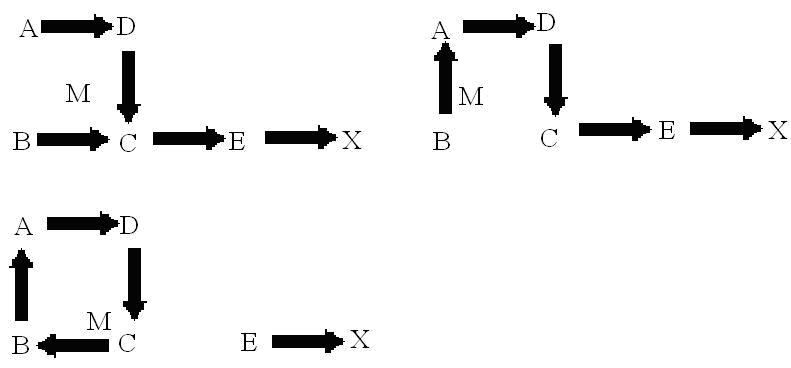
Fig 3: Impersonation in creating Loops
In fig 3, a malicious attacker M can form a routing loop so that none of the four nodes can reach the destination. To start the attack, M changes its MAC address to match A’s, moves closer to B and out of the range of A. It then sends an RREP to B that contains a hop count to X that is less than the one sent by C, for example zero. B therefore changes its route to the destination, X, to go through A. M then changes its MAC address to match B’s, moves closer to C and out of range of B, and then sends to C an RREP with a hop count to X lower than what was advertised by E. C then routes to X through B. At this point a loop is formed and X is unreachable from the four nodes.
Lack of integrity and authentication in routing protocols can further be exploited through “fabrication” referring to the generation of bogus routing messages. Fabrication attacks cannot be detected without strong authentication means and can cause severe problems ranging from denial of service to route subversion.
A more subtle type of active attack is the creation of a tunnel (or wormhole) in the network between two colluding malicious nodes linked through a private connection bypassing the network. This exploit allows a node to short-circuit the normal flow of routing message creating a virtual vertex cut in the network that is controlled b the two colluding attackers.
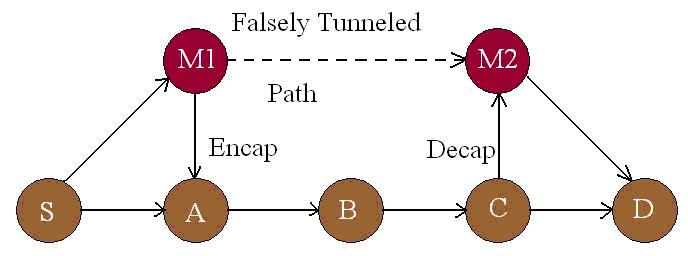
Fig 4: Worm Hole Attack
In the fig 4, M1 & M2 are malicious nodes collaborating to misrepresent available path lengths by tunneling route request packets. Solid lines denote actual paths between nodes, the thin line denotes the tunnel, and the dotted line denotes the path that M1 and M2 falsely claim is between them. Let us say that node S wishes to form a route to D and initiates route discovery. When M1 receives a RDP from S, M1 encapsulates the RDP and tunnels it to M2 through an existing data route, in this case {M1àAàBàCàM2}. When M2 update the packet header to reflect that the RDP, it forwards the RDP on to D as if it had only travelled {SàM1àM2àD}. Neither M1 nor M2 update the packet header to reflect that the RDP also travelled the path {AàBàC}. After route discovery, it appears to the destination that there are two routes from S of unequal length: {SàAàBàCàD} and {SàM1àM2àD}. If M2 tunnels the RREP back to M1, S would falsely consider the path to D via M1 a better choice (in terms of path length) than the path to D via A.
Another exposure of current Ad Hoc routing protocol is due to node selfishness that results in lack of cooperation among Ad Hoc nodes. A selfish node that wants to save battery life, CPU cycles and bandwidth for its own communication can endanger the correct network operation by simply not participating in the routing protocol or by not forwarding packets and dropping them whether control or data packets. This type of attack is called the black-hole attack. Current Ad Hoc routing protocols do not address the selfishness problem and assumes that all nodes in the MANET will cooperate to provide the required network functionalities.
Routing Protocols’ Security Requirements
To solve security issue in an Ad Hoc network and make it secure we have to look at a number of requirements that have to be achieved. These requirements are: availability, confidentiality, integrity, authentication and the non-repudiation.
- Availability: The network must at all times be available to send and receive messages despite if it is under attack. An attack can be in the form of a denial of service or an employed jamming to interface with the communication. Other possible threats to the availability are if an attacker disrupts the routing protocol or some other high-level service and disconnects the network. The node itself can also be the problem to availability. This is if the node is selfish and will not provide its services for the benefit of other nodes in order to save its own resources like, battery power.
- Confidentiality: Provides secrecy to sensitive material being sent over the network. This is especially important in a military scenario where strategic and tactical information is sent. If this information is sent. If this information would fall into enemy hands it could have devastating ramifications.
- Integrity: It ensures that messages being sent over the network are not corrupted. Possible attacks that would compromise the integrity are malicious attacks on the network or benign failures in the form of radio signal failures.
- Authentication: It ensures the identity of the nodes in the network. If A is sending to B, A knows that it is B who is receiving the message. Also B knows that it is A who is sending the message. If the authentication is not working, it is possible for an outsider to masquerade a node and then be able to send and receive messages without anybody noticing it, thus gaining access to sensitive information.
- Non-Repudiation: It makes possible for a receiving node to identify another node as the origin of a message. The sender cannot deny having sent the message and are therefore responsible for its contents. It is particularly useful for detection of compromised nodes.
However, because there are so many threats to protect from, there cannot be a general solution to them all. Also different applications will have different applications will have different security requirements to take into consideration. As a result of this diversity, many different approaches have different security requirements to take into consideration. As a result of this diversity, many different approaches have been made which focus on different parts of the problems. In the coming section, a comparison of some of the existing secure mobile Ad Hoc routing protocols with respect to most of the fundamental performance parameters will be given.
Secure Ad Hoc Routing Protocols
Throughout the exhaustive research and readings in the field of mobile Ad Hoc networks and the many security challenges and issues related to their routing protocols, analysis of various secure routing protocols proposed in the literature has been performed.
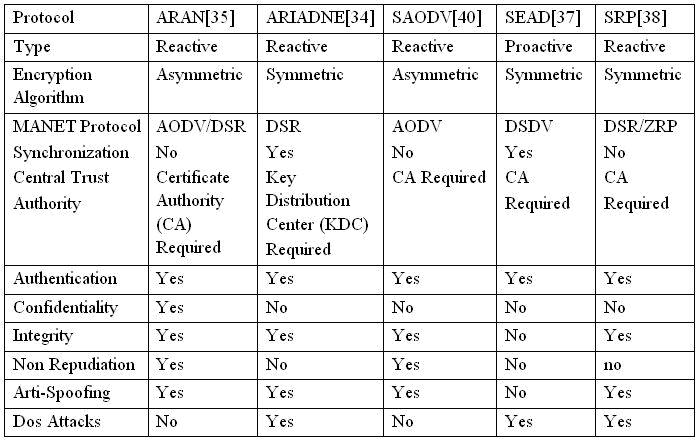
As a result, in the table 2, a comparison between some of the most established secure routing protocols with respect to some performance and security parameters is given so that to facilitate the choice of one of them to work on.
Table 2: Secure Ad Hoc Routing Protocols Comparison
Mobile Ad Hoc Networks Characteristics and Challenges
MANETs have several significant characteristics and challenges. They are as follows:
- Dynamic topologies: Nodes are free to move arbitrarily. Thus, the network topology may change randomly and rapidly at unpredictable times, and may consist of both bidirectional and unidirectional links.
- Bandwidth-Constrained, Variable Capacity Links: Wireless links will continue to have significantly lower capacity than their hardwired counterparts. In addition, the realized throughput of wireless communications, after accounting for the effects of multiple access, fading, noise, and interference conditions, is often much less than a radio’s maximum transmission rate.
- Energy-Constrained Operation: Some or all of the nodes in a MANET may rely on batteries or other exhaustible means for their energy. For these nodes, the most important system design optimization criteria may be energy conservation.
- Security: Mobile wireless networks are generally more prone to physical security threats than fixed-cable nets. The increased possibility of eavesdropping, spoofing, selfish behavior and denial-of-service attacks should be carefully considered.
These characteristics and challenges create a set of underlying assumptions and performance concerns for protocol design which extend beyond those guiding the design of routing within the higher-speed, semi-static topology of the fixed Internet.
Conclusion
The field of MANETs is rapidly growing and changing. While there are still many challenges that need to be met, it is likely that such networks will see widespread use within the next few years. One of these challenges is security. Security of mobile Ad Hoc networks has recently gained momentum in the research community. Due to the open nature of Ad Hoc networks and their inherent lack of infrastructure, security exposures can be an impediment to basic network operation and countermeasures should be included in network functions from the early stages of their design. Security solutions for MANER have to cope with a challenging environment including scarce energy and computational resources and lack of persistent structure to rely on for building trust.
Throughout this survey a discussion of existing mobile Ad Hoc networks’ routing protocols’ types and their advantages and disadvantages were given and a list of existing proactive, reactive and secure MANET routing protocols was compiled. Then, the different types of attacks targeting MANET routing protocols’ security were explored. In this presentation the fundamental requirements for the design of a secure routing protocol to defend against these security breaches was given. Furthermore, a comparison between some of the existing secure mobile Ad Hoc routing protocols was presented.
References
- E. Royer and C. Toh. A review of current routing protocols for Ad Hoc mobile wireless networks. IEEE personal communications, April 1999, pages 46-55.
- L. Zhou and Z. Haas. Securing Ad Hoc networks. IEEE networks Special issue on network security. November/December 1999, pages 24-30.
- Freesoft. Distance Vector Algorithms. http://www.freesoft.org/CIE/RFC/1058/6.htm.
- Wikipedia, The free Encyclopedia. http://en.wikipedia.org/wiki/Distance-vector_routing_protocol.
- Firewall. The site for Networking Professionals. http://www.firewall.cx/link_state.php.
- R. Duggirala. A Novel Route Maintenance Technique for Ad Hoc Routing Protocols. M.S. Thesis, University of Cincinnati, November 2000.