Technical Paper Title: ARTIFICIAL NEURAL NETWORK FOR HOME SECURITY SYSTEM(ANNHSS)
Authors:Anil Naik, 3rd Year BTech,Electronics and Telecommunications
College: Sardar Patel Institute of Technology, Mumbai University
Abstract— An Artificial Neural Network(ANN) which is a data processing system consisting of large number of highly interconnected processing elements (neurons) in multiple layers inspired by the structure of human brain that follows a Backpropagation Algorithm can be implemented as a Home Security System. This paper also points the drawbacks of the conventional methods of security like cryptography and how neural networks are effective in terms of reducing complexity and increasing speed and accuracy in a Home security system. This paper also suggests the implementation techniques for such a security system involving Neural Network Toolbox in MATLAB which provides simpler training, adaptation and simulation of the ANN.
Keywords—Artificial Neural Network, Home Security, MATLAB
1. INTRODUCTION
Now-a-days there are a lot of security systems that promises to provide excellent security to the residential apartments or houses, but in spite of that many of them fail to deliver when it comes to real time testing (burglary or crime events).For example in case of a house system secured by cryptography using password authentication technique, they do not assure foolproof security as at times they keep constraints like limiting the passwords to eight characters only, converting everything to lower case, etc. unfortunately this makes them more easy to be hacked.
A cryptographic system can only be as strong as the encryption algorithms, digital signature algorithms, one-way hash functions, and message authentication codes it relies on. And just as it’s possible to build a weak structure using strong materials, it’s possible to build a weak cryptographic system using strong algorithms and protocols which are more complex and difficult to implement. Encryption algorithms don’t necessarily provide data integrity [1].
The home security system using Neural Network which is suggested here is harder to be hacked. The Neural Network is used to train (learning) the identification parameters like UserID and password. Such a network acts as a brain in securing of passwords without constraints. One of the most well known types of neural network is the Multilayer Perceptrons Neural Network (MLPs).Such a perceptron network makes use of Backpropagation Algorithm which is a supervised artificial neural network (ANN) [2].Here, Resilient Backpropagation Technique is used to accelerate the training epochs [3]. Using this system it is safe
enough for the user to combine the door lock with the security system because it is hard for the intruder to hack the system and get the UserID and password. After the user enters the key, this system can be integrated as an authorization system before entering the house. Therefore, even if the key gets robbed, it would be difficult for strangers to access the door because it is hard to crack the owner’s UserID and password.
2. NEURAL NETWORK ARCHITECTURE AND TRAINING ALGORITHM
A) ANN’s
Artificial Neural Networks (ANNs) are programs designed to solve any problem by trying to mimic structure and function of our nervous system. Neural networks are based on simulated neurons which are joined together in a variety of ways to form networks [4].
Neural network resembles the human brain in the following two ways: –
-A neural network acquires knowledge through learning.
-A neural network’s knowledge is stored within the interconnection strengths known as synaptic weight.
Neural network are typically organized in layers. Layers are made up of a number of interconnected ‘nodes’, which contain an ‘activation function’. Patterns are presented to the network via the ‘input layer’, which communicates to one or more ‘hidden layers’ where the actual processing is done via a system of weighted ‘connections’. The hidden layers then link to an ‘output layer’ where the answer is output.ANN is represented in the Fig1.
The first layer is the input layer and the last one, the output layer. The layers that are placed within these two are the middle or hidden layers. A neural network is a system that emulates the cognitive abilities of the brain by establishing recognition of particular inputs and producing the appropriate output. Neural networks are not “hard-wired” in particular way;
|
they are trained using presented inputs to establish their own internal weights and relationships guided by feedback. They
adapt on their own, they are usually adjusted, or trained so that a particular input leads to a specific target output [4].
B) Learning
The ability to learn is a fundamental trait of intelligence. A learning process in the ANN context can be viewed as the problem of updating network architecture and connection weights, so that a network can efficiently perform a specific task. There are three main learning paradigms:
-Supervised
-Unsupervised
-Hybrid
These learning’s are classified depending upon whether the network is to be trained with/without the presence of a supervisor (teacher) [4].
There are several training methods used for training of ANN:
1. Back propagation network (BPN)
2. Radial basis function network (RBF)
3. Levenberg-Marquardt network (LMN)
4. Hopfield network
C) Resilient Backpropagation Algorithm (RBPN)
As the algorithm’s name implies, the errors (and therefore the learning) propagate backwards from the output nodes to the inner nodes. So technically speaking, backpropagation is used to calculate the gradient of the error of the network with respect to the network’s modifiable weights. This gradient is almost always then used in a simple Gradient Descent Algorithm to find weights that minimize the error.
The gradient descent algorithms are not suitable for using with multilayer networks. This is mainly because of the fact that these networks typically use the sigmoid or the tan-sigmoid activation functions. The slope of the sigmoid and the tan-sigmoid functions approach zero when the input is large. This effect causes the weights to be updated by only a minute fraction, when using the gradient descent algorithm, although they are far from their optimal value [4].
The Resilient Backpropagation algorithm considers only the sign of the gradient to determine the direction of the weight update. The size of the weight change is governed by a separate update value. This method therefore eliminates the effects of the magnitudes of partial derivatives. In this method, if the derivative of performance function has the same sign for two successive iterations, with respect to the current weight, then the updated value is increased. The updated value is decreased in case the derivative with respect to the current weight changes signs from the previous iteration. The update value remains constant if the derivative is zero. If the weights tend to oscillate, then the weight change will be reduced. And finally, if the weight continues to change in the same direction for several iterations, the magnitude of weight change is increased. This algorithm is more robust and facilitates faster convergence than the steepest descent algorithms; hence, it is apt for multilayer feed-forward networks [5].
3. HOME SECURITY SYSTEM IMPLEMENTATION
A) UserID and password requirements
UserID’s and passwords are the most common form of authentication in use today. Inspite of the improved mechanisms over which authentication information can be carried; most systems usually require a password as the token against which initial authorization is performed. Due to the conflicting goals that good password maintenance schemes must meet, passwords are often the weakest link in authentication architecture. This can be only partially addressed by technical remedies. The implementation of authentication systems should measure risks and benefits against an appropriate threat model and protection target.
UserID’s have few requirements for security that some basic restriction should be implemented in the system to make them distinct. UserID’s that are derivations of a real name or actual real names can clearly give personal detail clues to an attacker.
Password quality refers to the entropy of a password and is necessary to ensure the security of the users’ accounts. A good password is a password that is impossible to guess by other people. The password is suggested should at least contain 8 characters, one alphanumeric, one mixed case and at least one special character (not A-Z or 0-9) to make the password robust.
B) Encoding
This is a mandatory step as the inputs that we are dealing with are alphanumeric (characters, numbers, symbols etc.) and the system used is a neural network which deals with binary numbers. Hence, the inputs must be converted into their binary equivalent which could be their own ASCII codes. The only requirement is to feed (or train) the network with the data that we encode through the encoder.
C) Neural Network Implementation
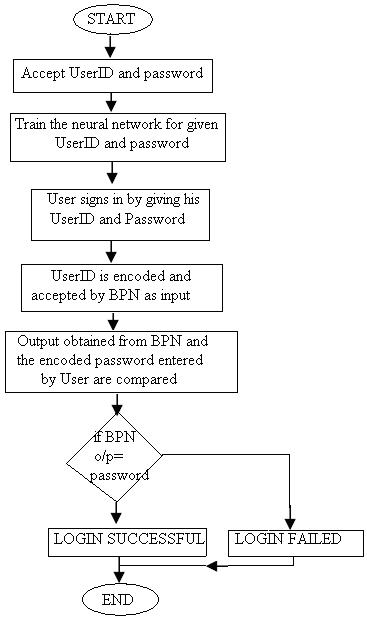
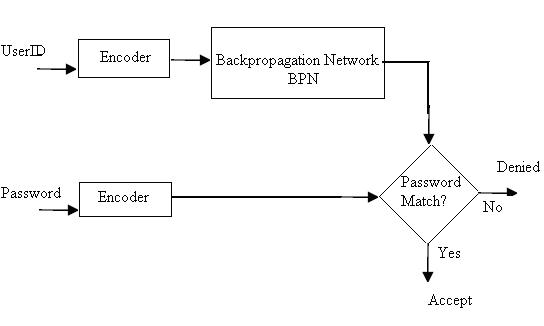
System will be initialized on the first instance, wherein the user will provide an appropriate UserID and password. Training of the data is done after the users have registered the User ID and password, and before the users are able to login the system. The UserID will be accepted by the input layer of the neural network as the input and the password will hence be considered as the target. Such an input/output pair will be used to train the neural network using the RBPN for thousands of epochs for better learning. Once the training is done the system is ready to work, when the User enters the UserID and password, the encoded UserID is taken as an input to the BPN, which performs the algorithm and produces an output. Now, this output is compared with the encoded password which was entered by the user. If they match, the Login is successful and the user is genuine else the access is denied.
Fig2.Flowchart for the ANNHSS
Fig3.Block Diagram Representation for ANNHSS
The flowchart for developing the Security System is shown in Fig2. and
Its corresponding Block Diagram has been illustrated in Fig 3.
D) Software Suggested: Neural Network Toolbox in MATLAB by The MathWorks
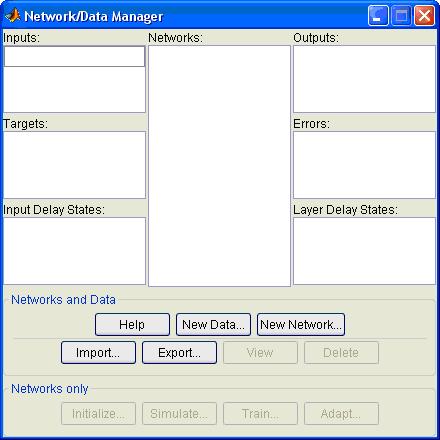
The Neural Network Toolbox in MATLAB provides nntool which provides a Network/Data Manager window, which allows you to import, create, use, and export neural networks and data. It supports training algorithms provides the settings to set neuron layers, weights, bias etc. and can be trained for ‘n’ number of epochs to train the
network and obtain an accurate output [6].
nntool in MATLAB:
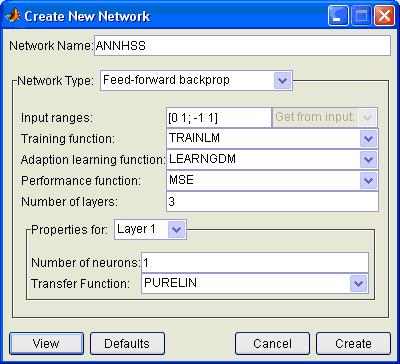
New network created (ANNHSS):
This window allows setting of the training parameters, weights, bias and trains the network for a number of epochs when the User inputs his UserID and password.
This is multilayer Artificial Neural Network created
This problem can be made more efficient and user-interactive by implementing a GUI in MATLAB and interfacing the above Neural Network with it, so as to achieve the goal of implementing an Artificial Neural Network Home Security System.
4. BENEFITS AND PRACTICALITY
Unlike public key cryptography which required exponential computing and complex programming, the process of BPN only requires simple multiplication and addition to obtain the result [4].Hence, when a user wants to enter the house, the system could respond with the result either to accept or reject the user’s request.
The use of neural networks provides the benefit to eliminate the disadvantages of maintaining the conventional verification table which not only requires memory to store but also reduces the speed of the operation. Hence, by using ANN the conventional verification table can be made redundant and the speed of operation increases.
5. CONCLUSION
A House Security System by using Artificial Neural Network can be developed successfully by the above suggested methods. It is known that as the number of hidden neurons increases, the training time and number of epochs to train the network increases proportionately. This problem was removed by embedding a local adaptive technique, Resilience BPN, for which the training time is very short.
We proved that BPN is a better method as compared to cryptography and has been employed in our problem to recall the relationship of User ID and Password that had been registered, as ANN acts as a “brain” in itself once trained. Hence, it could be used to replace the verification table used in the conventional system.
We also witnessed how MATLAB can be effectively used to implement the security system as it has simpler training, adaptation and simulation methods.
6. REFERENCES
[1] Bruce Schneier, “Security Pitfalls in Cryptography” 1998.
[2] I.C.Lin, H.H. Ou, M.S. Hwang, “A user Authentication System using Back-propagation Network,” Neural Comput & Applic, June 2005
[3] S.Z. Reyhani, M. Mahdavi, “User Authentication Using Neural Network in Smart Home Networks,” International Journal of Smart Home, Vol 1 no 2, pp147, July 2007.
[4] “Introduction to Artificial Neural Network”, by Jacek M. Zurada; Jaico Publishing House, 1999
[5] H. Demuth, M.Beale, M.Hagan, “Neural Network Toolbox TM User Guide: Faster Training,” Natick: The MathworksTM Inc, 2008.
[6] Software:MATLAB (“The MathWorks”)
Author’s work:
– A thorough and comprehensive study of Artificial Neural Network using Back Propagation Algorithm was done.
-Study of conventional methods like cryptography was done from the articles online.
-Found out the pitfalls in the conventional method of cryptography by researching online.
-Similarly, the benefits of using ANN, its practicality, cost effectiveness, simplicity in simulation was studied.
-Studied Neural Network Toolbox from MATLAB to simulate neural networks.
-Personally implemented a small Backpropagation Algorithm in MATLAB to minutely study the network adaptation and its simulation.
-Reference books were used which are mentioned above.